Zero trust is regarded as an innovative security architecture of the future — and as we all know, the future is now. The increased complexity and rising security requirements in digital space mean that new security approaches are needed. But what exactly is zero trust? And what role can artificial intelligence (AI) play in this respect?
Recent years have been characterized by rapidly advancing digitalization, continuous evolution of technology, and a sharp increase in the proportion of remote work as a consequence of the coronavirus pandemic. These factors alone have prompted more urgent calls for new security approaches. Stricter requirements for application and security rules along with the dramatic rise in the number of (successful) cyberattacks on companies and government agencies have further underscored the pressing nature of this necessity. New innovative solutions are essential for security in digital space — in the EU as well as in Germany. The zero trust principle in combination with novel AI technology offers a possible means for finding the needed answers.
Zero trust is a visionary security architecture based on the guiding principle of not trusting any device, user, or service, whether inside or outside the organization. The current procedure is to designate devices as fundamentally trustworthy subsequent to one-time authentication, and they are then allowed to move freely in the network as a general principle. The zero trust principle demands the revalidation of all devices and users at all times. Authorizations are kept to a minimum — both scope and time — and are rigorously enforced. They are issued in observance of the principle of the smallest number of permissions needed to complete the job. Furthermore, all data, whether transmitted or stored, are encrypted. Artificial intelligence can further reinforce this claim of high security because it is able to recognize certain reactions and behavior patterns more quickly as well as to determine the prioritization of risk, initiating and successfully realizing any risk mitigation measures that may be expedient as quickly as possible (see Figure).
A comprehensive zero trust-AI architecture can be achieved solely through the interaction of all components of the IT infrastructure. Every single communication request, even those above the network layer, must be classified per se as untrustworthy and authenticated separately. These checks and the resulting approvals/blocks to communications must be available in real time and around the clock. Any transformation in this direction must take place successively, and any interdependencies among the technologies just as the correct timing of the measures must be taken into account. The human factor in particular must not be neglected again.
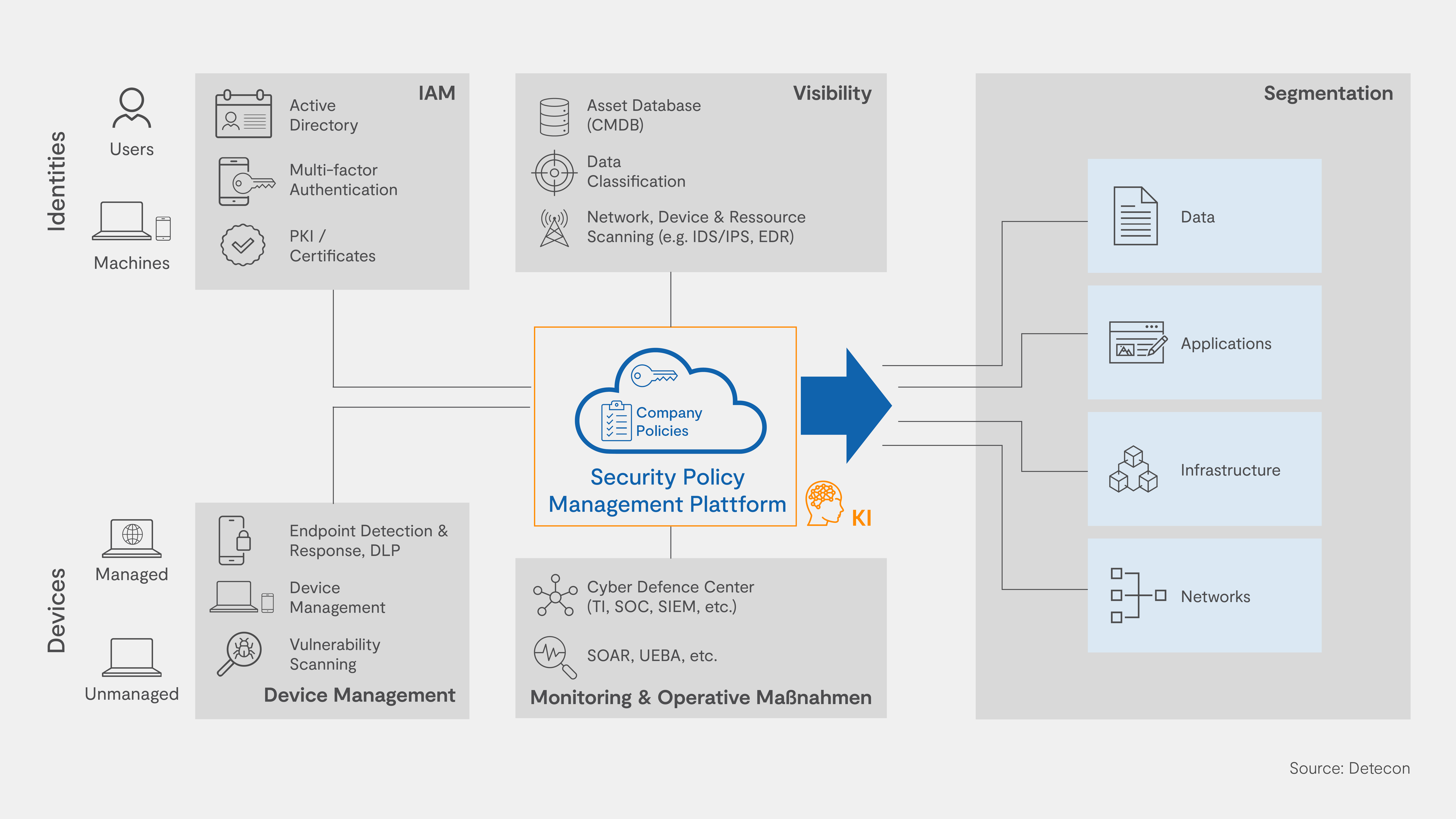
Implementing a zero trust architecture requires a clear and aligned understanding of the core components and of the supporting tools and processes. A step-by-step implementation is recommended to ensure that the functional capability of a large organization is maintained.. The prioritization must be determined as appropriate to any given organization. If this holistic approach is taken, not only can the transformation to zero trust succeed, but digitalization aligned with the demands of the future can also be driven forward — for a secure digital environment in the long term.









