"Microsoft servers unavailable for days". What if this headline would become true? Then you would possibly not even be able to read this text here, because your operating system would not work. But not only your operating system, but also those of many organizations. You would be unable to work, and German administrations and public organizations would be similarly affected. They also work predominantly with Microsoft applications. The consequences of this total failure are unimaginable. But this problem can be prevented by organizations following the adage "don't put all your eggs in one basket", IT experts say "prevention through digital sovereignty and protection against digital dependencies".
Digital sovereignty is more than developing your own solutions
The topic of digital sovereignty is gaining momentum. This is because digital sovereignty is much more than the ability of an organization or a state to provide and maintain both IT applications and IT infrastructure itself. Digital sovereignty means being able, both as an individual and as an institution, to move in the digital world (1) independently, (2) self-determined and (3) securely (Competence Center Public IT). It is a matter of working with solutions that correspond to one's own values and legal concepts.
Germany pushed the issue of digital sovereignty during its EU Council presidency and is building GAIA-X, a European data infrastructure, together with France and other European partners. The German government has also committed to maintaining key national defense industrial technologies, again in cooperation with European partners. But this raises new questions. What role must the state play? What does digital sovereignty mean in the field of security and defense organizations?
Digital sovereignty in the area of BOS
Due to the sovereign and governmental obligation of authorities and organizations with security tasks (BOS) to protect citizens and the state, digital sovereignty is of particular importance for these organizations. This must be anchored in strategic as well as operational functions and areas. On the one hand, the consideration of protection against intentional and deliberately induced digital dependency plays a role here. On the other hand, there is also the digital dependency that may even "creep in" as a result of market developments, political, demographic and social changes.
The goal must therefore be to achieve and maintain digital sovereignty to the extent necessary.
Achieving greater digital sovereignty in four steps
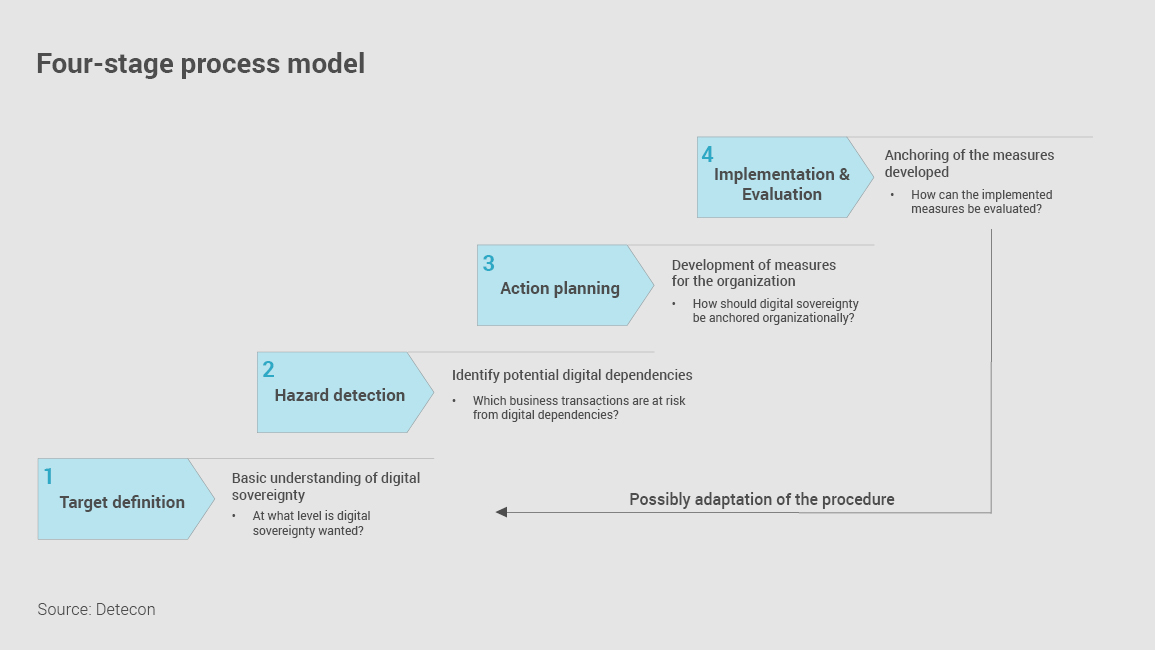
Four basic steps are recommended for this purpose:
- Define a basic understanding of Digital Sovereignty for one's own organization and derive the target picture and priority action areas.
Questions: At what level is digital sovereignty desired? To be sovereign on national level or on European level or rather on NATO level? Is digital sovereignty enough or should it even escalate to digital autarky? Where is there an increased risk to the fulfillment of my business mission through digital dependencies? - Related to the action areas: Identify the potential sources of digital dependency and the resulting risks measured against the business mission of the respective organization.
Questions: Which business cases are at risk from digital dependency? How does the way of working need to change to achieve the desired level of digital sovereignty? - Develop measures to avert and prevent the identified risks and locate the measures and affected business cases in the respective areas of the organization (e.g., strategy, purchasing, HR, CIO).
Questions: How should the topic be anchored organizationally? How can employees be sensitized to the topic of digital sovereignty? - Implementation and anchoring of the developed measures in the organization and monitoring of the concrete risks / incidents that have occurred and the measures initiated as a result.
Questions: How can the measures taken be evaluated in terms of their contribution to greater digital sovereignty? How should digital sovereignty be anchored in operational management?
The continuous review between the target definition (aspiration) and the measures actually implemented (reality) as well as the balancing of both parameters must be taken into account in the procedure. If necessary, the measures and the target definition must be adjusted again after the evaluation.
Digital sovereignty as an overall task for all organizational departments.
The approach described involves the entire organization and ensures that the level of digital sovereignty meets the current requirements of the business mission. Selected examples show how broad the influence and scope of the pursuit of digital sovereignty are.
Risk management and internal control systems ensure that risks derived from the business mission are identified and managed.
Purchasing and procurement ensure that aspects of digital sovereignty are taken into account in every procurement process. They manage the portfolio of suppliers and ensure that dependencies on individual suppliers are avoided. In addition, requirements from Risk Management and Legal are met in relation to Digital Sovereignty.
Human Resources Management and Development enable the provision of the required experts and related skills to ensure Digital Sovereignty.
The CIO area designs, procures and implements digital solutions and thus has a central role in creating as well as maintaining the organization's Digital Sovereignty. The task here is to develop appropriate guidelines and architecture specifications. These must be implemented in such a way that the ability to design digital solutions in line with the Digital Sovereignty defined by the organization is maintained.
External players, such as academia and consultants, enable a transfer of knowledge from theory and practice into the company's own organization. Through these new impulses, the so-called "look beyond the edge of the table" can take place and new paths can be pointed out.

IT development planning as a decisive success factor.
The aforementioned areas of the organization must cooperate closely and make decisions at the points relevant to Digital Sovereignty in a coordinated manner that is focused on the overall benefit to the organization.
To enable this coordinated and concerted decision making, (IT) development planning can play a central role. It makes it possible to firmly as well as permanently anchor digital sovereignty in all areas of the organization by taking an integrative and overarching view of the organization's IT landscape. This requires that it involves the supporting corporate functions (see above) and integrates them into the operational implementation.
This applies all the more to public IT service providers, as they have a dual task and must ensure not only their own digital sovereignty but also that of their customers.
Digital sovereignty means teamwork
The above examples show how diverse the implications and the fields of action are in the pursuit of digital sovereignty. It is therefore important to recognize that digital sovereignty can only be achieved through the interaction of many functions in the organization. This requires a coordinated collaborative approach.
In addition to the organization's internal team members, external experts also play a role. A trusting interplay between all players forms the basis for jointly achieving greater Digital Sovereignty in line with the organization's own and shared organizational values and norms.
Ultimately, digital sovereignty does not mean isolation, but rather self-determined action with self-selected partners, and ideally not tomorrow, but already yesterday.
Source:
Competence Center Public IT (2020): Digital Sovereignty as Strategic Autonomy (german only) Digitale Souveränität als strategische Autonomie (oeffentliche-it.de)